
Hackers suspected of working for the Chinese government are mass exploiting a pair of critical vulnerabilities that give them complete control of virtual private network appliances sold by Ivanti, researchers said.
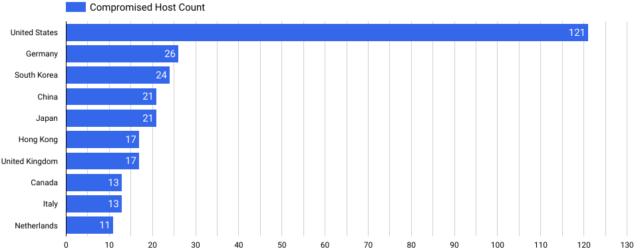
As of Tuesday morning, security company Censys detected 492 Ivanti VPNs that remained infected out of 26,000 devices exposed to the Internet. More than a quarter of the compromised VPNs—121—resided in the US. The three countries with the next biggest concentrations were Germany, with 26, South Korea, with 24, and China, with 21.
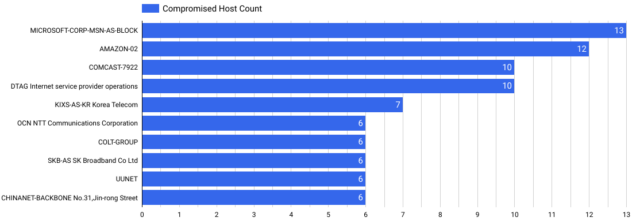
Microsoft’s customer cloud service hosted the most infected devices with 13, followed by cloud environments from Amazon with 12, and Comcast at 10.
“We conducted a secondary scan on all Ivanti Connect Secure servers in our dataset and found 412 unique hosts with this backdoor, Censys researchers wrote. “Additionally, we found 22 distinct ‘variants’ (or unique callback methods), which could indicate multiple attackers or a single attacker evolving their tactics.”
In an email, members of the Censys research team said evidence suggests that the people infecting the devices are motivated by espionage objectives. That theory aligns with reports published recently by security firms Volexity and Mandiant. Volexity researchers said they suspect the threat actor, tracked as UTA0178, is a “Chinese nation-state-level threat actor.” Mandiant, which tracks the attack group as UNC5221, said the hackers are pursuing an “espionage-motivated APT campaign.”
All civilian governmental agencies have been mandated to take corrective action to prevent exploitation. Federal Civilian Executive Branch agencies had until 11:59 pm Monday to follow the mandate, which was issued Friday by the Cybersecurity and Infrastructure Security Agency. Ivanti has yet to release patches to fix the vulnerabilities. In their absence, Ivanti, CISA, and security companies are urging affected users to follow mitigation and recovery guidance provided by Ivanti that include preventative measures to block exploitation and steps for customers to rebuild and upgrade their systems if they detect exploitation.
“This directive is no surprise, considering the worldwide mass exploitation observed since Ivanti initially revealed the vulnerabilities on January 10,” Censys researchers wrote. “These vulnerabilities are particularly serious given the severity, widespread exposure of these systems, and the complexity of mitigation—especially given the absence of an official patch from the vendor as of the current writing.
When Avanti disclosed the vulnerabilities on January 10, the company said it would release patches on a staggered basis starting this week. The company has not issued a public statement since confirming the patch was still on schedule.
VPNs are an ideal device for hackers to infect because the always-on appliances sit at the very edge of the network, where they accept incoming connections. Because the VPNs must communicate with broad parts of the internal network, hackers who compromise the devices can then expand their presence to other areas. When exploited in unison, the vulnerabilities, tracked as CVE-2023-46805 and CVE-2024-21887, allow attackers to remotely execute code on servers. All supported versions of the Ivanti Connect Secure—often abbreviated as ICS and formerly known as Pulse Secure—are affected.
The ongoing attacks use the exploits to install a host of malware that acts as a backdoor. The hackers then use the malware to harvest as many credentials as possible belonging to various employees and devices on the infected network and to rifle around the network. Despite the use of this malware, the attackers largely employ an approach known as “living off the land,” which uses legitimate software and tools so they’re harder to detect.
The posts linked above from Volexity and Mandiant provide extensive descriptions of how the malware behaves and methods for detecting infections.
Given the severity of the vulnerabilities and the consequences that follow when they’re exploited, all users of affected products should prioritize mitigation of these vulnerabilities, even if that means temporarily suspending VPN usage.
