
On Friday, Colonial Pipeline took many of its systems offline in the wake of a ransomware attack. With systems offline to contain the threat, the company’s pipeline system is inoperative. The system delivers approximately 45 percent of the East Coast’s petroleum products, including gasoline, diesel fuel, and jet fuel.
Colonial Pipeline issued a statement Sunday saying that the US Department of Energy is leading the US federal government response to the attack. “[L]eading, third-party cybersecurity experts” engaged by Colonial Pipeline itself are also on the case. The company’s four main pipelines are still down, but it has begun restoring service to smaller lateral lines between terminals and delivery points as it determines how to safely restart its systems and restore full functionality.
Colonial Pipeline has not publicly said what was demanded of it or how the demand was made. Meanwhile, the hackers have issued a statement saying that they’re just in it for the money.
Regional emergency declaration
In response to the attacks on Colonial Pipeline, the Biden administration issued a Regional Emergency Declaration 2021-002 this Sunday. The declaration provides a temporary exemption to Parts 390 through 399 of the Federal Motor Carrier Safety Regulations, allowing alternate transportation of petroleum products via tanker truck to relieve shortages related to the attack.
The emergency declaration became effective immediately upon issuance Sunday and remains in effect until June 8 or until the emergency ends, whichever is sooner. Although the move will ease shortages somewhat, oil market analyst Gaurav Sharma told the BBC the exemption wouldn’t be anywhere near enough to replace the pipeline’s missing capacity. “Unless they sort it out by Tuesday, they’re in big trouble,” said Sharma, adding that “the first areas to hit would be Atlanta and Tennessee, then the domino effect goes up to New York.”
Russian gang DarkSide believed responsible for attack
Unnamed US government and private security sources engaged by Colonial have told CNN, The Washington Post, and Bloomberg that the Russian criminal gang DarkSide is likely responsible for the attack. DarkSide typically chooses targets in non-Russian-speaking countries but describes itself as “apolitical” on its dark web site.
Infosec analyst Dmitry Smilyanets tweeted a screenshot of a statement the group made this morning, apparently concerning the Colonial Pipeline attack:
NBC News reports that Russian cybercriminals frequently freelance for the Kremlin—but indications point to a cash grab made by the criminals themselves this time rather than a state-sponsored attack.
Dmitri Alperovitch, former CTO of infosec company CrowdStrike, claims that direct Russian state involvement hardly matters at this point. “Whether they work for the state or not is increasingly irrelevant, given Russia’s obvious policy of harboring and tolerating cybercrime,” he said.
DarkSide “operates like a business”
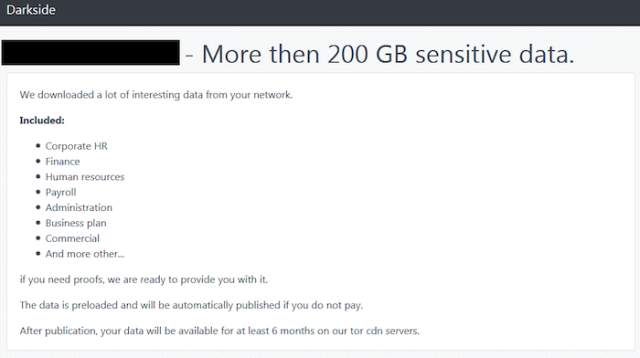
London-based security firm Digital Shadows said in September that DarkSide operates like a business and described its business model as “RaaC”—meaning Ransomware-as-a-Corporation.
In terms of its actual attack methods, DarkSide doesn’t appear to be very different from smaller criminal operators. According to Digital Shadows, the group stands out due to its careful selection of targets, preparation of custom ransomware executables for each target, and quasi-corporate communication throughout the attacks.
DarkSide claims to avoid targets in medical, education, nonprofit, or governmental sectors—and claims that it only attacks “companies that can pay the requested amount” after “carefully analyz[ing] accountancy” and determining a ransom amount based on a company’s net income. Digital Shadows believes these claims largely translate to “we looked you up on ZoomInfo first.”
It seems quite possible that the group didn’t realize how much heat it would bring onto itself with the Colonial Pipeline attack. Although not a government entity itself, Colonial’s operations are crucial enough to national security to have brought down immediate Department of Energy response—which the group certainly noticed and appears to have responded to via this morning’s statement that it would “check each company that our partners want to encrypt” to avoid “social consequences” in the future.
