
Human weaknesses are a rich target for phishing attacks. Making humans click “Don’t Allow” over and over again in a phone prompt that can’t be skipped is an angle some iCloud attackers are taking—and likely having some success.
Brian Krebs’ at Krebs on Security detailed the attacks in a recent post, noting that “MFA Fatigue Attacks” are a known attack strategy. By repeatedly hitting a potential victim’s device with multifactor authentication requests, the attack fills a device’s screen with prompts that typically have yes/no options, often very close together. Apple’s devices are just the latest rich target for this technique.
Both the Kremlin-backed Fancy Bear advanced persistent threat group and a rag-tag bunch of teenagers known as Lapsus$ have been known to use the technique, also known as MFA prompt bombing, successfully.
If the device owner is annoyed by the sudden sound or deluge of notifications (which essentially block access to other phone features) or just considers the prompt too quickly and has trained themselves to click “Yes”/”Allow” to most other prompts, they may click “Allow” and give the attackers the access they need. Or, having to dismiss so many prompts, their thumb or finger might simply hit the wrong pixel and accidentally let the bad folks in.
Parth Patel, an AI startup founder, detailed a March 22 attack on himself in a thread on X (formerly Twitter). Parth said that his Apple phone, watch, and laptop all received “100+ notifications” asking to use those devices to reset his Apple password. Given the nature of the prompt, they can’t be ignored or dismissed until acted upon, all but locking up the devices.
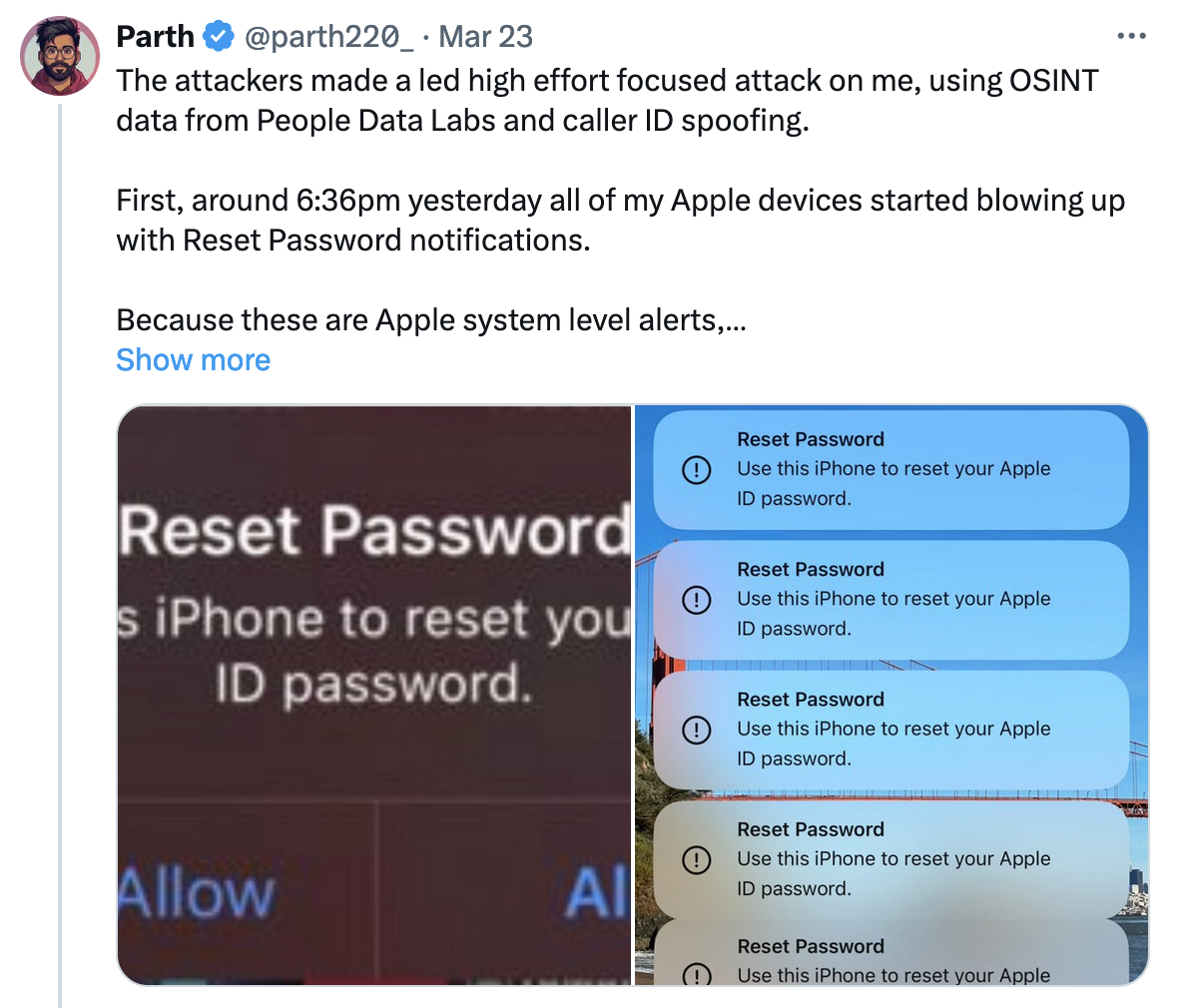
Having dismissed the alerts, Parth then received a call that was spoofed to appear as if it were coming from Apple’s official support line. Parth asked them to validate information about him, and the callers had his date of birth, email, current address, and former addresses available. But Parth, having previously queried himself on people search sites, caught the caller using one of the names frequently tied into his reports. The caller also asked for an Apple ID code sent by SMS, the kind that explicitly follows up with “Don’t share it with anyone.”
Another target told Krebs that he received reset notifications for several days, then also received a call purportedly from Apple support. After the target did the proper thing—hung up and called Apple back—Apple unsurprisingly had no record of a support issue. The target told Krebs that he traded in his iPhone and started a new iCloud account but still received password prompts—while at the Apple Store for his new iPhone.
Not Apple’s first encounter with rate limiting
From these tales, as well as another detailed on Krebs’ site, it’s clear that Apple’s password-reset scheme needs rate limiting or some other form of access control. It’s also worth noting that FIDO-compliant MFA is immune to such attacks.
You only need a phone number, an email (which Apple provides the first letters for, on either side of the “@”), and to fill out a short CAPTCHA to send the notification. And it’s not an exaggeration to say that you can’t do much of anything on an iPhone when the prompt is present, having tried to get into any other app when I pushed a reset prompt on myself. I managed to push three prompts in a few minutes, although at one point, a prompt blocked me and told me that there was an error. I switched to another browser and continued to spam myself with no issue.
As noted by one of Krebs’ sources and confirmed by Ars, receiving the prompt on an Apple Watch (or at least some sizes of Apple Watch) means only seeing an “Allow” button to tap and just a hint of a button below it before scrolling down to tap “Don’t Allow.”
Ars has reached out to Apple for comment on the issue and will update this post with any new information. Apple has a support article regarding phishing messages and phony support calls, noting that anyone getting an unsolicited or suspicious phone call from Apple should “just hang up” and report it to the FTC or local law enforcement.
Apple has previously addressed denial-of-service-like attacks in AirDrop. Kishan Bagaria, creator of texts.com, detailed a way in which Apple’s device-to-device sharing system could be overwhelmed with AirDrop share requests. Apple later fixed the bug in iOS 13.3, thanking Bagaria for their discovery. Now, when an Apple device declines an AirDrop request three times, it will automatically block future such requests.
Security vendor BeyondTrust’s essential advice for preventing MFA fatigue attacks involves limiting the number of authentication attempts in a time window, blocking access after failed attempts, adding geolocation or biometric requirements, increasing access factors, and flagging high-volume attempts.
This post was updated to note a support article from Apple regarding phishing calls.
Listing image by Kevin Purdy
