
Network hardware-maker QNAP is urging customers to update their network-attached storage devices immediately to protect them from a new wave of ongoing ransomware attacks that can destroy terabytes of data in a single stroke.
Singapore-based QNAP said recently that it has identified a new campaign from a ransomware group known as DeadBolt. The attacks take aim at QNAP NAS devices that use a proprietary feature known as Photo Station. The advisory instructs customers to update their firmware, suggesting there is a vulnerability that’s under exploit, but the company makes no explicit mention of a CVE designation that security professionals use to track such security flaws.
“To protect your NAS from the DeadBolt ransomware, QNAP strongly recommends securing your QNAP NAS devices and routers by following these instructions,” company officials wrote:
- Disable the port forwarding function on the router
- Set up myQNAPcloud on the NAS to enable secure remote access and prevent exposure to the Internet
- Update the NAS firmware to the latest version
- Update all applications on the NAS to their latest versions
- Apply strong passwords for all user accounts on the NAS
- Take snapshots and back up regularly to protect your data
The advisory applies to the following devices:
- QTS 5.0.1: Photo Station 6.1.2 and later
- QTS 5.0.0/4.5.x: Photo Station 6.0.22 and later
- QTS 4.3.6: Photo Station 5.7.18 and later
- QTS 4.3.3: Photo Station 5.4.15 and later
- QTS 4.2.6: Photo Station 5.2.14 and later
DeadBolt first appeared in January, and within a few months, Internet security scanning service Censys said the ransomware had infected thousands of QNAP devices. The company took the unusual step of automatically pushing the update to all devices, even those that had automatic updating turned off.
Now, DeadBolt is back. Users first learn of the infection in ransom notes like this one:
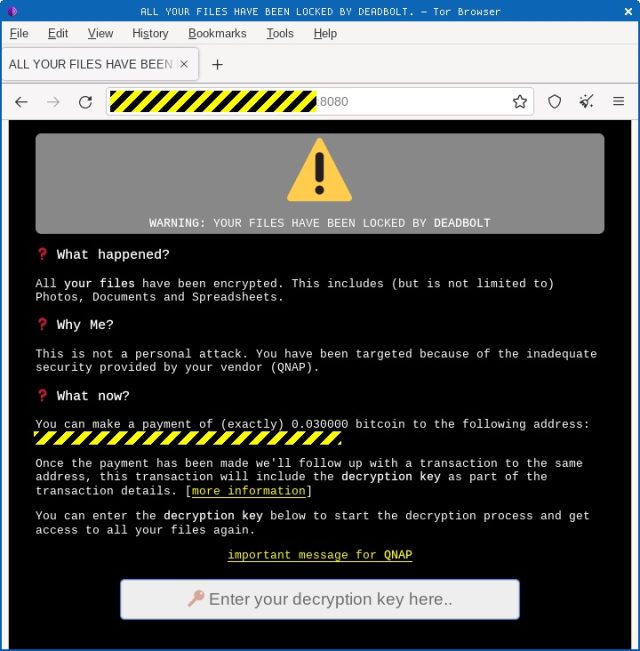
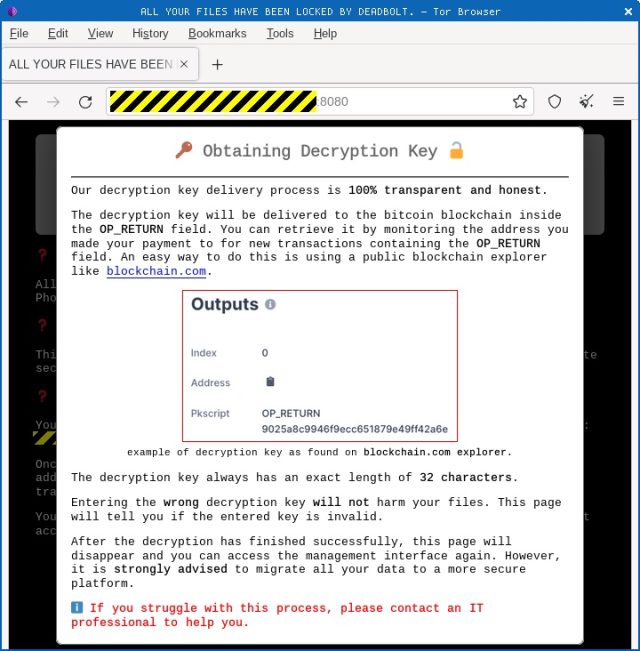
DeadBolt personnel also provide instructions for obtaining the decryption key needed to recover encrypted files as well as a proposal to QNAP to purchase a master decryption key that the company could pass along to infected customers.
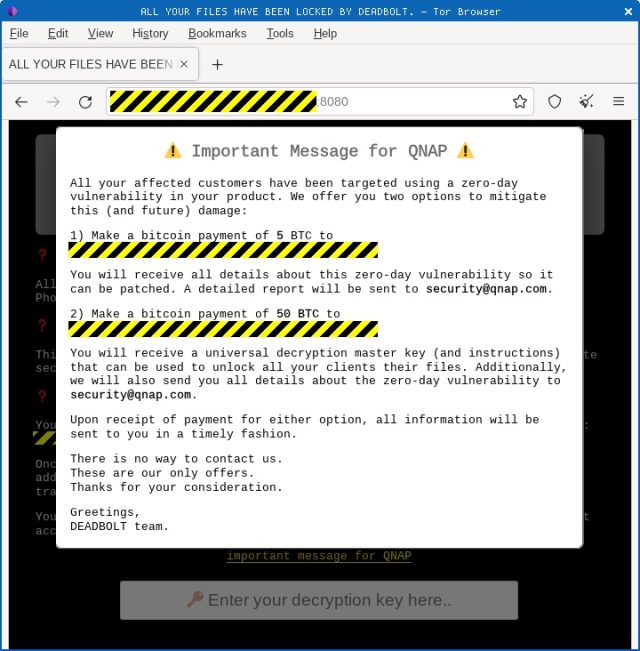
So far, there’s no indication that QNAP intends to avail itself of this opportunity.
NAS devices typically connect directly to a router to make files available to everyone on a home or small office network. NAS boxes can also be configured to make files available over the Internet. Configuring the devices to be secure under these circumstances can be fraught, particularly when there’s the possibility of undisclosed vulnerabilities.
QNAP’s latest advisory, linked above, provides guidance on setting up QNAP’s proprietary myQNAPcloud service. Given the sensitivity of the data stored on many such devices, users should invest ample time to ensure they’re following best practices.
