
Microsoft’s Edge browser has replaced Internet Explorer in almost every regard, but some exceptions remain. One of those, deep inside Microsoft Word, was exploited by a North-Korean-backed group this fall, Google security researchers claim.
It’s not the first time the government-backed APT37 has utilized Internet Explorer’s lingering presence, as Google’s Threat Analysis Group (TAG) notes in a blog post. APT37 has had repeated success targeting South Korean journalists and activists, plus North Korean defectors, through a limited but still successful Internet Explorer pathway.
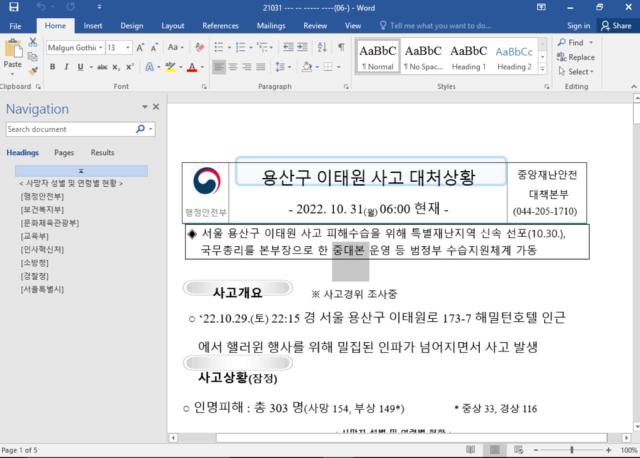
The last exploit targeted those heading to Daily NK, a South Korean site dedicated to North Korean news. This one involved the Halloween crowd crush in Itaewon, which killed at least 151 people. A Microsoft Word .docx document, named as if it were timed and dated less than two days after the incident and labeled “accident response situation,” started circulating. South Korean users began submitting the document to the Google-owned VirusTotal, where it was flagged with CVE-2017-0199, a long-known vulnerability in Word and WordPad.
Just as in April 2017, the document, if you click to allow Word/WordPad to view it outside the no-download “Protected View,” downloads a rich text template from an attacker-controlled server, then grabs more HTML that looks like Rich Text Format templates. Office and WordPad intrinsically use Internet Explorer to render HTML in what Microsoft describes as “specially crafted files,” giving attackers a way to then bring in various malware payloads. While patched that same month, the vulnerability persisted; it was one of the vectors exploited in a Petya wave more than a year later.
The specific vulnerability has to do with Internet Explorer’s JavaScript engine. An error during just-in-time optimization leads to a data type confusion and memory writing. This particular exploit also cleaned up after itself, clearing the Internet Explorer cache and history of its presence. While Google’s TAG doesn’t know what payloads were delivered, APT37 has previously circulated exploits that triggered BLUELIGHT, ROKRAT, and DOLPHIN, all focusing on North Korean political and economic interests. (North Korean hackers aren’t averse to a Chrome exploit, though.)
Microsoft patched the specific exploit in its JScript engine, but this being the fifth year of remote-code Word doc attacks, it seems like they’ll be around for a while longer. And North Korean actors will be eager to act on them.
