
Two new studies suggest that ransomware isn’t the lucrative, enterprise-scale gotcha it used to be. Profits to attackers’ wallets, and the percentage of victims paying, fell dramatically in 2022, according to two separate reports.
Chainalysis, a blockchain analysis firm that has worked with a number of law enforcement and government agencies, suggests in a blog post that based on payments to cryptocurrency addresses it has identified as connected to ransomware attacks, payments to attackers fell from $766 million in 2021 to $457 million last year. The firm notes that its wallet data does not provide a comprehensive study of ransomware; it had to revise its 2021 total upward from $602 for this report. But Chainalysis’ data does suggest payments—if not attacks—are down since their pandemic peak.
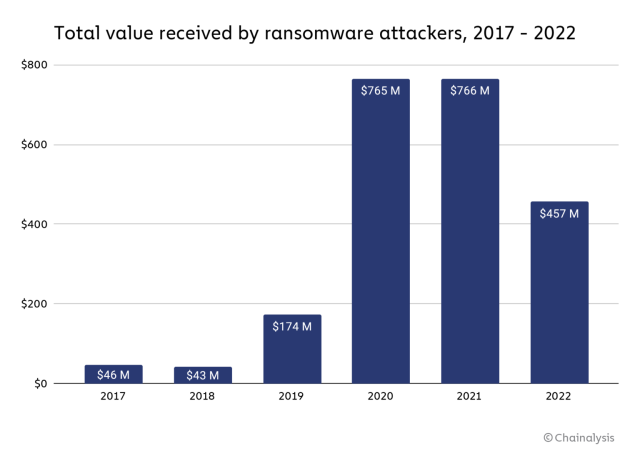
Chainalysis’ post also shows attackers switching between malware strains more quickly, and more known attackers are keeping their funds in mainstream cryptocurrency exchanges instead of the illicit and funds-mixing destinations that were more popular in ransomware boom times. This might look like a sign of a mature market with a higher cost of entry. But there’s more to it than typical economics, Chainalysis suggests.
Smaller attackers often switch between different ransomware-as-a-service (RaaS) vendors performing various kinds of A/B tests on targets. And specific strains of malware bring different risk factors to ransom negotiations. When Conti, a major ransomware strain, was found to be coordinating with the Kremlin and Russia’s Federal Security Service (FSB), victims had another reason—government sanctions—not to pay up. CD Projekt Red, maker of the games Cyberpunk 2077 and The Witcher, was one of the notable holdouts.
Conti’s leaders split up and ended up working inside a number of other ransomware groups, Chainalysis notes. So while ransomware may look like a huge market with thousands of participants, it’s still a small, traceable group of core actors that can be monitored.
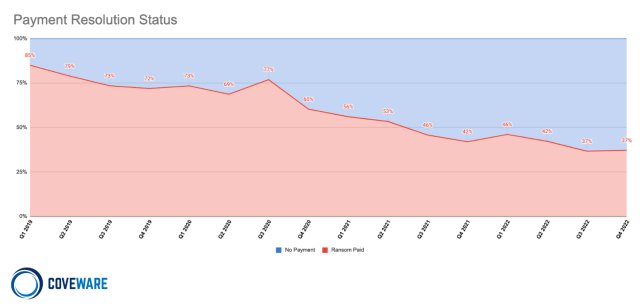
Cybersecurity analysis firm Coveware is seeing similar trends, reporting that victims paying fell from 85 percent in Q1 of 2019 to 37 percent in Q4 2022. The firm pins this on investments in security and response planning, improvements in law enforcement recovering funds and arresting actors, and the compounding effects of fewer payments pushing ransomware attackers out of the market.
-
Coveware’s data suggests a marked spike in the average and median ransomware payments in the last quarter of 2022.
-
The median size of ransomware victims has been climbing steadily but has spiked in the last half of 2022, according to Coveware’s data.
Most of that lines up with Chainalysis’ report, but Coveware has a few surprising statistics. The average and median ransom payments rose considerably in the last quarter of 2022 from just the quarter before. The median size of a ransomware victim also rose, with a particular spike to record levels in the last half of 2022. Coveware suggests this is another result of the non-payment squeeze on attackers. Targeting larger firms allows for a larger upfront demand, and more firms are attempting to re-extort victims—something previously practiced only by smaller firms targeting smaller companies. “RaaS groups care less than their predecessors about upholding their reputation,” Coveware’s post explains. “Ransomware actors are first and foremost driven by economics, and when the economics are dire enough, they will stoop to levels of deception and duplicity to recoup their losses.”
More data, charts, and examples can be found at the blog posts of Chainalysis and Coveware, as first spotted by Dark Reading.
