
Over the past few months, geopolitical tensions have escalated as Russia amassed tens of thousands of troops along Ukraine’s border and made subtle but far-reaching threats if Ukraine and NATO don’t agree to Kremlin demands.
Now, a similar dispute is playing out in cyber arenas, as unknown hackers late last week defaced scores of Ukrainian government websites and left a cryptic warning to Ukrainian citizens who attempted to receive services.
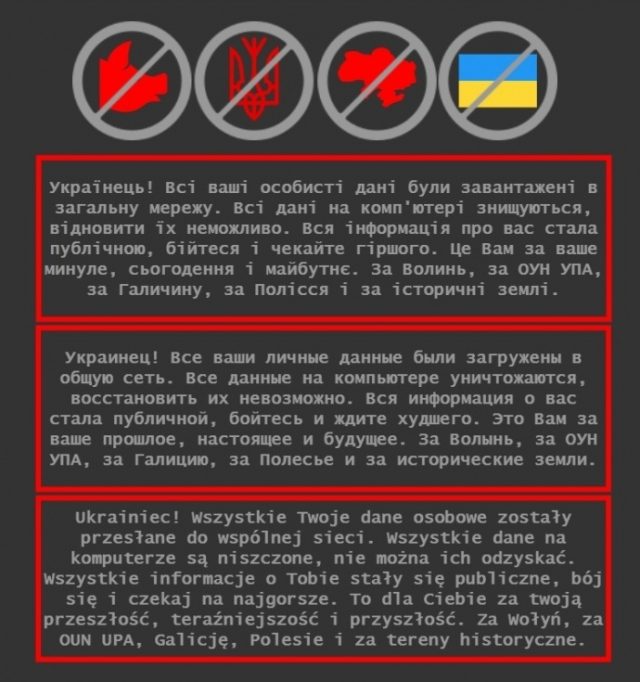
Be afraid and expect the worst
“All data on the computer is being destroyed, it is impossible to recover it,” said a message, written in Ukrainian, Russian, and Polish, that appeared late last week on at least some of the infected systems. “All information about you has become public, be afraid and expect the worst.”
Around the same time, Microsoft said in a post over the weekend, “destructive” malware with the ability to permanently destroy computers and all data stored on them began appearing on the networks a dozens of government, nonprofit, and information technology organizations, all based in Ukraine. The malware—which Microsoft is calling Whispergate—masquerades as ransomware and demands $10,000 in bitcoin for data to be restored.
But Whispergate lacks the means to distribute decryption keys and provide technical support to victims, traits that are found in virtually all working ransomware deployed in the wild. It also overwrites the master boot record—a part of the hard drive that starts the operating system during bootup.
“Overwriting the MBR is atypical for cybercriminal ransomware,” members of the Microsoft Threat Intelligence Center wrote in Saturday’s post. “In reality, the ransomware note is a ruse and that the malware destructs MBR and the contents of the files it targets. There are several reasons why this activity is inconsistent with cybercriminal ransomware activity observed by MSTIC.”
Over the weekend, Serhiy Demedyuk, deputy head of Ukraine’s National Security and Defense Council, told news outlets that preliminary findings from a joint investigation of several Ukrainian state agencies show that a threat actor group known as UNC1151 was likely behind the defacement hack. The group, which researchers at security firm Mandiant have linked to the government of Russian ally Belarus, was behind an influence campaign named Ghostwriter.
Ghostwriter worked by using phishing emails and theft domains that spoof legitimate websites such as Facebook to steal victim credentials. With control of content management systems belonging to news sites and other heavily trafficked properties, UNC1151 “primarily promoted anti-NATO narratives that appeared intended to undercut regional security cooperation in operations targeting Lithuania, Latvia, and Poland,” authors of the Mandiant report wrote.
All evidence points to Russia
Ukrainian officials said UNC1151 was likely working on behalf of Russia when it used its skill in harvesting credentials and infiltrating websites to deface Ukraine’s government sites. In a statement, they wrote:
As of now, we can say that all the evidence points to the fact that Russia is behind the cyber attack. Moscow continues to wage a hybrid war and is actively building forces in the information and cyberspace.
Russia’s cyber-troops are often working against the United States and Ukraine, trying to use technology to shake up the political situation. The latest cyber attack is one of the manifestations of Russia’s hybrid war against Ukraine, which has been going on since 2014.
Its goal is not only to intimidate society. And to destabilize the situation in Ukraine by stopping the work of the public sector and undermining the confidence in the government on the part of Ukrainians. They can achieve this by throwing fakes into the infospace about the vulnerability of critical information infrastructure and the “drain” of personal data of Ukrainians.
Damage assessment
There were no immediate reports of the defacements having a destructive effect on government networks, although Reuters on Monday reported Ukraine’s cyber police found that last week’s defacement appeared to have destroyed “external information resources.”
“A number of external information resources were manually destroyed by the attackers,” the police said, without elaborating. The police added: “It can already be argued that the attack is more complex than modifying the homepage of websites.”
Microsoft, meanwhile, didn’t say if the destructive data wiper it found on Ukrainian networks had merely been installed for potential use later on or if it had actually been executed to wreak havoc.
There’s no proof that the Russian government had any involvement in the wiper malware or the website defacement, and Russian officials have flatly denied it. But given past events, Russian involvement wouldn’t be a surprise.
In 2017, a massive outbreak of malware initially believed to be ransomware shut down computers around the world and resulted in $10 billion in total damages, making it the most costly cyberattack ever.
NotPetya initially spread spread through a legitimate update module of M.E.Doc, a tax-accounting application that’s widely used in Ukraine. Both Ukrainian
and US government officials have said Russia was behind the attacks. In 2020, federal prosecutors charged four Russian nationals for alleged hacking crimes involving NotPetya.
