
Researchers have uncovered yet another supply chain attack targeting an open source code repository, showing that the technique, which has gained wide use in the past few years, isn’t going away anytime soon.
This time, the repository was PyPI, short for the Python Package Index, which is the official software repository for the Python programming language. Earlier this month, a contributor with the username Lolip0p uploaded three packages to PyPI titled: colorslib, httpslib, and libhttps. The contributor was careful to disguise all three as legitimate packages, in this case, as libraries for creating a terminal user interface and thread-safe connection pooling. All three packages were advertised as providing full-featured usability.
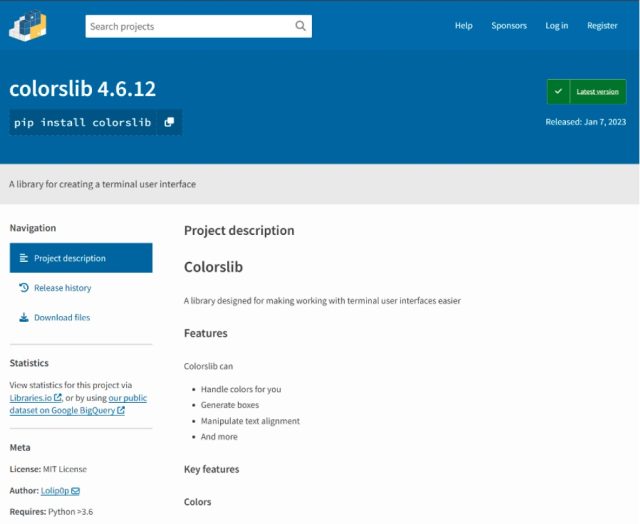
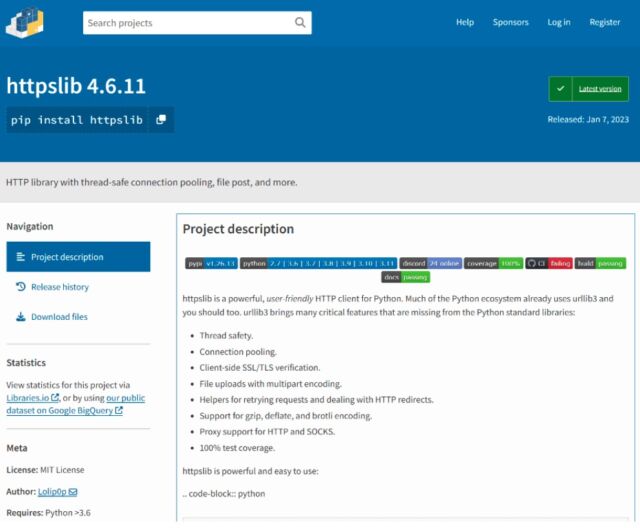
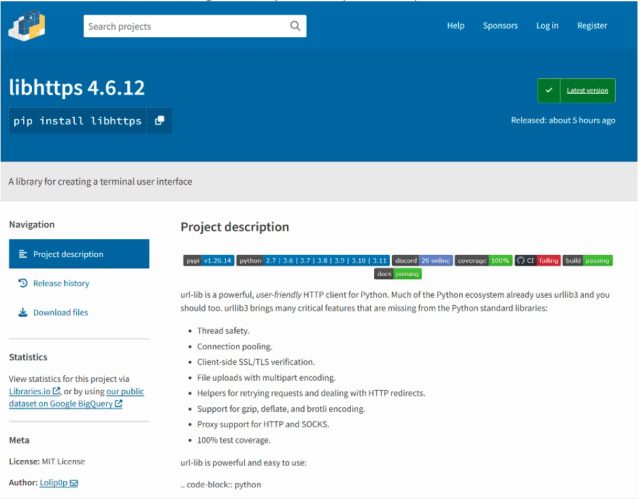
Researchers from security firm Fortinet said all three packages were malicious, and the setup.py script for them was identical. The files opened a Powershell window and downloaded a malicious file, called Oxzy.exe, which at the time of the discovery, was detected by only three antimalware providers.
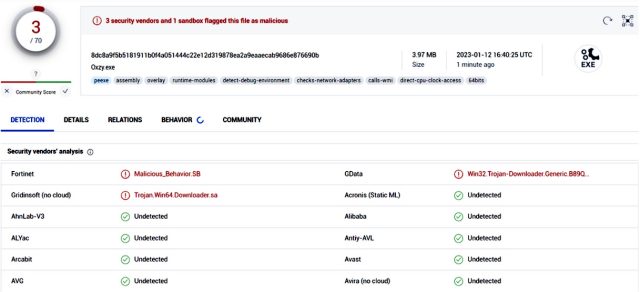
Oxzy.exe, in turn, downloaded a second malicious file titled Update.exe, which was detected by only seven antimalware engines.
The last file to be dropped was named SearchProtocolHost.exe, which was detected by nine engines.
One of those engines was Microsoft’s Defender. The description was Wacatac.b!ml, a piece of malware that Microsoft said “can perform a number of actions of a malicious hacker’s choice on your PC.” An analysis from Trend Micro showed that the Trojan has existed since at least 2019, when it was being spread through pirated software available online.
Open source repositories such as PyPI and NPM have become increasingly used as vectors for installing malware through supply chain attacks, which spread malicious software at the source of a legitimate project. From 2018 to 2021, this type of attack grew on NPM almost fourfold and about fivefold on PyPI, according to security firm ReversingLabs. From January to October last year, 1,493 malicious packages were uploaded to PyPI and 6,977 malicious packages were uploaded to NPM.
Last September, PyPI supply chain attacks escalated. A threat actor launched a credential phishing attack on PyPI contributors and, when successful, used the access to compromised accounts to publish malware that posed as the latest release for legitimate projects associated with the account. Legitimate projects included Exotel and Spam. In contrast to malicious packages that used names that appeared similar to well-known projects, these attacks were able to poison the official source of a project used for years. The threat actor behind the attacks has existed since at least 2021.
“Python end users should always perform due diligence before downloading and running any packages, especially from new authors,” ReversingLabs researchers wrote in the post documenting the latest attacks. “And as can be seen, publishing more than one package in a short time period is no indication that an author is reliable.”
The same advice should be applied to NPM, RubyGems, and virtually every other open source repository.
