For years, Israeli digital forensics firm Cellebrite has helped governments and police around the world break into confiscated mobile phones, mostly by exploiting vulnerabilities that went overlooked by device manufacturers. Now, Moxie Marlinspike—the brainchild behind the Signal messaging app—has turned the tables.
On Wednesday, Marlinspike published a post that reported vulnerabilities in Cellebrite software that allowed him to execute malicious code on the Windows computer used to analyze a device. The researcher and software engineer exploited the vulnerabilities by loading specially formatted files that can be embedded into any app installed on the device.
Virtually no limits
“There are virtually no limits on the code that can be executed,” Marlinspike wrote.
He continued:
For example, by including a specially formatted but otherwise innocuous file in an app on a device that is then scanned by Cellebrite, it’s possible to execute code that modifies not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way (inserting or removing text, email, photos, contacts, files, or any other data), with no detectable timestamp changes or checksum failures. This could even be done at random, and would seriously call the data integrity of Cellebrite’s reports into question.
Cellebrite provides two software packages: The UFED breaks through locks and encryption protections to collect deleted or hidden data, and separate Physical Analyzer uncovers digital evidence (“trace events”).
To do their job, both pieces of Cellebrite software must parse all kinds of untrusted data stored on the device being analyzed. Typically, software that is this promiscuous undergoes all kinds of security hardening to detect and fix any memory-corruption or parsing vulnerabilities that might allow hackers to execute malicious code.
“Looking at both UFED and Physical Analyzer, though, we were surprised to find that very little care seems to have been given to Cellebrite’s own software security,” Marlinspike wrote. “Industry-standard exploit mitigation defenses are missing, and many opportunities for exploitation are present.”
Compromising integrity
One example of this lack of hardening was the inclusion of Windows DLL files for audio/video conversion software known as FFmpeg. The software was built in 2012 and hasn’t been updated since. Marlinspike said that in the intervening nine years, FFmpeg has received more than 100 security updates. None of those fixes are included in the FFmpeg software bundled into the Cellebrite products.
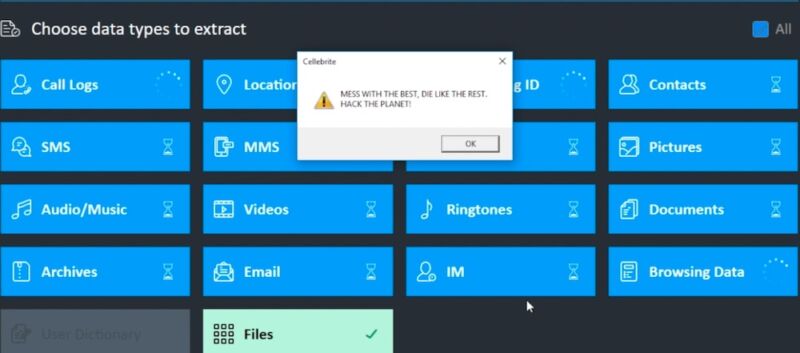
Marlinspike included a video that shows UFED as it parses a file he formatted to execute arbitrary code on the Windows device. The payload uses the MessageBox Windows API to display a benign message, but Marlinspike said that “it’s possible to execute any code, and a real exploit payload would likely seek to undetectably alter previous reports, compromise the integrity of future reports (perhaps at random!), or exfiltrate data from the Cellebrite machine.”
Marlinspike said he also found two MSI installer packages that are digitally signed by Apple and appear to have been extracted from the Windows installer for iTunes. Marlinspike questioned if the inclusion constitutes a violation of Apple copyrights. Neither Apple nor Cellebrite provided a comment before this post went live.
Marlinspike said he obtained the Cellebrite gear in a “truly unbelievable coincidence” as he was walking and “saw a small package fall off a truck ahead of me.” The incident does seem truly unbelievable. Marlinspike declined to provide additional details about precisely how he came into possession of the Cellebrite tools.
The fell-of-a-truck line wasn’t the only tongue-in-cheek statement in the post. Marlinspike also wrote:
In completely unrelated news, upcoming versions of Signal will be periodically fetching files to place in app storage. These files are never used for anything inside Signal and never interact with Signal software or data, but they look nice, and aesthetics are important in software. Files will only be returned for accounts that have been active installs for some time already, and only probabilistically in low percentages based on phone number sharding. We have a few different versions of files that we think are aesthetically pleasing, and will iterate through those slowly over time. There is no other significance to these files.
The vulnerabilities could provide fodder for defense attorneys to challenge the integrity of forensic reports generated using the Cellebrite software. Cellebrite representatives didn’t respond to an email asking if they were aware of the vulnerabilities or had plans to fix them.
“We are of course willing to responsibly disclose the specific vulnerabilities we know about to Cellebrite if they do the same for all the vulnerabilities they use in their physical extraction and other services to their respective vendors, now and in the future,” Marlinspike wrote.
Post updated to add fourth- and third-to-last paragraphs.
