
Of the 18,000 organizations that downloaded a backdoored version of software from SolarWinds, the tiniest of slivers—possibly as small as 0.2 percent—received a follow-on hack that used the backdoor to install a second-stage payload. The largest populations receiving stage two were, in order, tech companies, government agencies, and think tanks/NGOs. The vast majority—80 percent—of these 40 chosen ones were located in the US.
These figures were provided in an update from Microsoft President Brad Smith. Smith also shared some insightful and sobering commentary on the significance of this almost unprecedented attack. His numbers are incomplete, since Microsoft sees only what its Windows Defender app detects. Still, Microsoft sees a lot, so any difference with actual numbers is likely a rounding error.
Crème de la crème
SolarWinds is the maker of a nearly ubiquitous network management tool called Orion. A surprisingly large percentage of the world’s enterprise networks run it. Hackers backed by a nation state—two US senators who received private briefings say it was Russia—managed to take over SolarWinds’ software build system and push a security update infused with a backdoor. SolarWinds said about 18,000 users downloaded the malicious update.
The months-long hack campaign came to light only after security firm FireEye admitted it had been breached by a nation state. In the course of their investigation, company researchers discovered that the hackers used the Orion backdoor, not just against FireEye, but in a much broader campaign targeting multiple federal agencies. In the 10 days that have passed since, the scope and discipline of the hacking operation has become increasingly clear.
The hack on SolarWinds and its backdooring of 18,000 servers was only the attack’s first phase, one that was done only to zero in on the targets of interest. These crème de la crème organizations were likely the sole purpose for the entire operation, which lasted for at least nine months, and possibly much longer.
The Microsoft numbers illustrate just how targeted this attack was. The hackers behind this supply chain compromise had privileged access to 18,000 enterprise networks and followed up on only 40 of them.
The map below shows the sector of these elite hack victims.
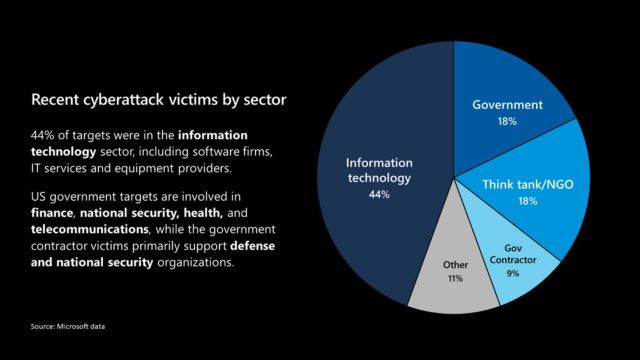
Breaching norms
Smith tacitly acknowledged that all industrialized nations engage in espionage that includes hacking. What was different this time, he said, was that a nation state had breached established norms by putting vast swaths of the world in real peril to pursue its ends. Smith went on to write:
It’s critical that we step back and assess the significance of these attacks in their full context. This is not “espionage as usual,” even in the digital age. Instead, it represents an act of recklessness that created a serious technological vulnerability for the United States and the world. In effect, this is not just an attack on specific targets, but on the trust and reliability of the world’s critical infrastructure in order to advance one nation’s intelligence agency. While the most recent attack appears to reflect a particular focus on the United States and many other democracies, it also provides a powerful reminder that people in virtually every country are at risk and need protection irrespective of the governments they live under.
Elsewhere in the post, Smith quoted FireEye CEO Kevin Mandia saying recently: “We are witnessing an attack by a nation with top-tier offensive capabilities.” Smith then wrote:
As Microsoft cybersecurity experts assist in the response, we have reached the same conclusion. The attack unfortunately represents a broad and successful espionage-based assault on both the confidential information of the U.S. Government and the tech tools used by firms to protect them. The attack is ongoing and is being actively investigated and addressed by cybersecurity teams in the public and private sectors, including Microsoft. As our teams act as first responders to these attacks, these ongoing investigations reveal an attack that is remarkable for its scope, sophistication and impact.
The SolarWinds hack is shaping up as one of the worst espionage hacks of the past decade if not of all time. The tradecraft and pinpoint accuracy is nothing short of astounding. As those elite victims over the next weeks unravel what the second stage did to their networks, this story is likely to go into hyperdrive.
